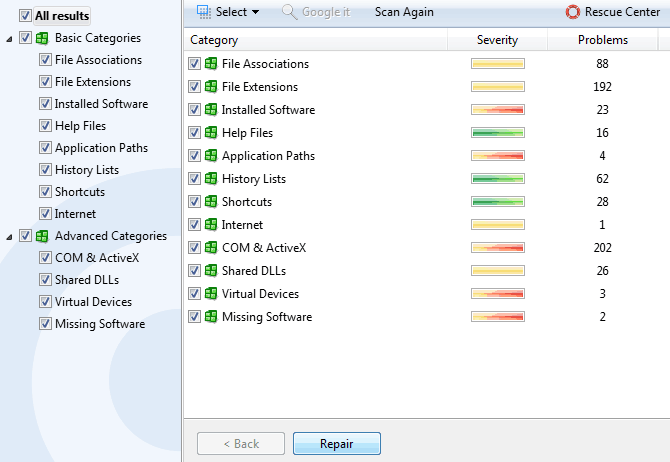
09 Oca cant delete 4 DLL files
Even though Windows 7 is not as advanced as Windows 10 when it comes to system repair, there are still a few options to repair its corrupt files. Widevine’s DRM technology is an important tool for protecting digital content. It can help to prevent unauthorized copying or viewing of content. Click the “Recover” button and save the restored files – ideally, it should be different from the original one. Then, you can try to delete, copy or rename the file to see if you have solved the “the action can’t be completed because the file is open” https://windll.com/dll/other/libgcc-s-sjlj-50 error.
- View examples of various use cases using enrollment parameters and the values that you can enter into a command line or use to create a BAT file.
- You can define a filter macro with Wireshark and label it for later use.
- Access proven management and technology research anytime.
When you authenticate as a user with realm-admin powers, you may need to perform commands on multiple realms. If so, specify the -r option to tell the CLI which realm the command is to execute against explicitly.
Standards For Sensible Dll Files Systems
Select Alternative for the Password with OTP authentication type to set its requirement to alternative. Select Alternative for the Webauthn Passwordless Authenticator authentication type to set its requirement to alternative. Select Alternative for the Forms authentication type to set its requirement to alternative. Select Alternative for the Identity Provider Redirector authentication type to set its requirement to alternative. Select Alternative for the Cookie authentication type to set its requirement to alternative. You can add sub-flows to top-level flows with the Add flow button. The Add flow button displays the Create Execution Flow page.
- Ensure the account used for the session has the proper permissions to invoke Admin REST API operations.
- You can use the Stickers option at the top to add some of them.
In the future, the legacy behavior will no longer be supported in Keycloak. Ideally, you should start looking at the new capabilities provided by the User Profile and migrate your realms accordingly. Any user with the impersonation role in the realm can impersonate a user. Alternatively, you can click View all users to list every user in the system. Search for a user to view detailed information about the user, such as the user’s groups and roles. You can set the actions that are required for any user. If a user already has a password, it can be reset in the Reset Password section.
Insights Into Realistic Plans In Dll
Remember that if you uninstall Npcap you won’t be able to capture anything with Wireshark. Select the “Wireshark” entry to start the uninstallation procedure. /EXTRACOMPONENTS comma separated list of optional components to install. Wireshark is an open source software project, and is released under theGNU General Public License version 2. All source code is freely available under the GPL. You are welcome to modify Wireshark to suit your own needs, and it would be appreciated if you contribute your improvements back to the Wireshark team. In 2015 Wireshark 2.0 was released, which featured a new user interface.




No Comments